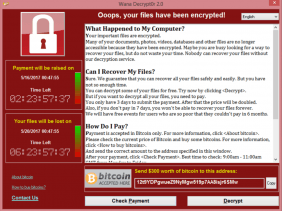
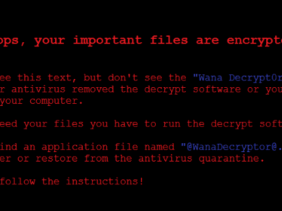
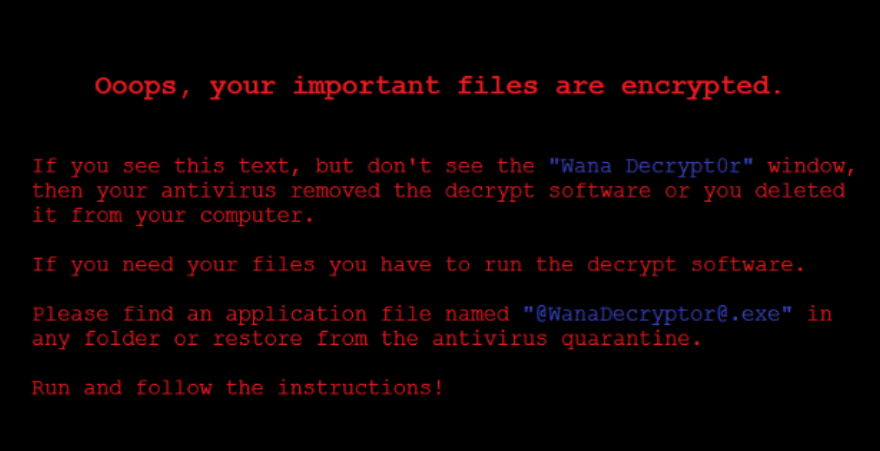
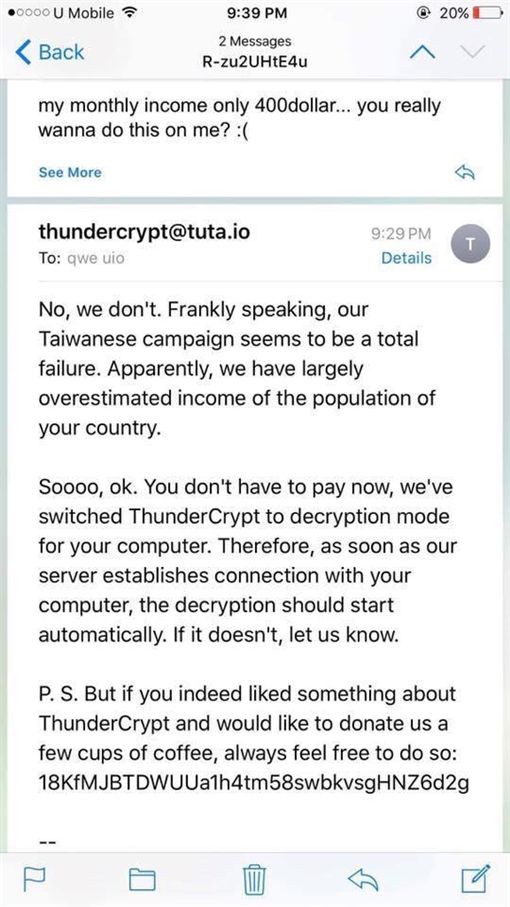
NHS and other PC owners suffered from a malware called Wannacry, that would later prompt the PC owners to pay at least the sum of $300 before they could get their files unlocked.
In a good news by Adrien Guinet, a French security researcher from Quarkslab, there is a new free decryption tool that works on Window XP, Vista, Window server 2003 and 2008.
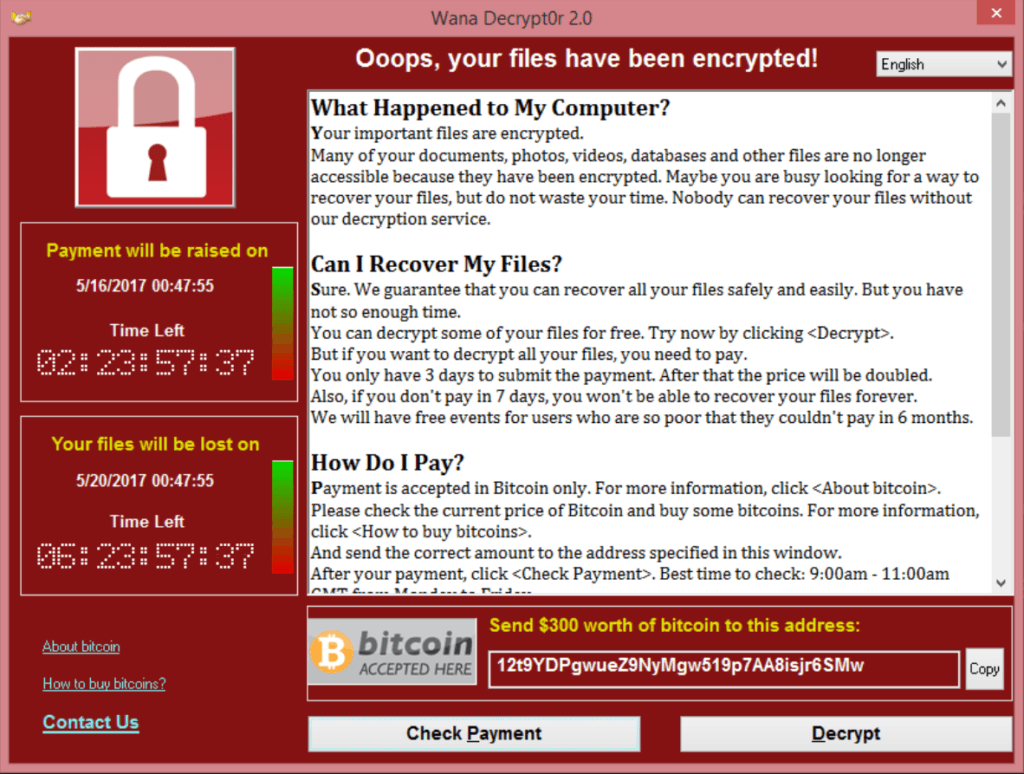
How Does Decryption Works
Like every other encryption techniques, the Wannacry fraud scheme works by generating the public and private key on victim's computer. It relies on prime numbers to encrypt and decrypt system files. To make sure the victim is not decrypting the key files, Wannacry ransomware then deletes the private key from the PC, leaving the user with one choice of asking from Wannacry department.
Adrien Guinet based on his research was able to provide an anti-wannacry, and it is called, Wannakey.
Wannakey basically tries to retrieve the two prime numbers used in the encryption, and try to generate the encryption key from memory. Wannakey was only able to do this because when the private key was deleted on victims PC, Wannacry did not delete it from memory.
This method only works on Windows XP.
Another available tool that works from Windows XP to Windows 7 is the Wannakiwi. According to Adrien;
It does so by searching for them in the wcry.exe process. This is the process that generates the RSA private key. The main issue is that the CryptDestroyKey and CryptReleaseContext does not erase the prime numbers from memory before freeing the associated memory.
The above will only work if the affected PC have not been rebooted after it was infected, and also if the memory has not been allocated to another PC.
To see if you can use any of these tools, it is advisable to download WanaKiwi tool from Github, and use it on the affected PC via the CMD
See Video